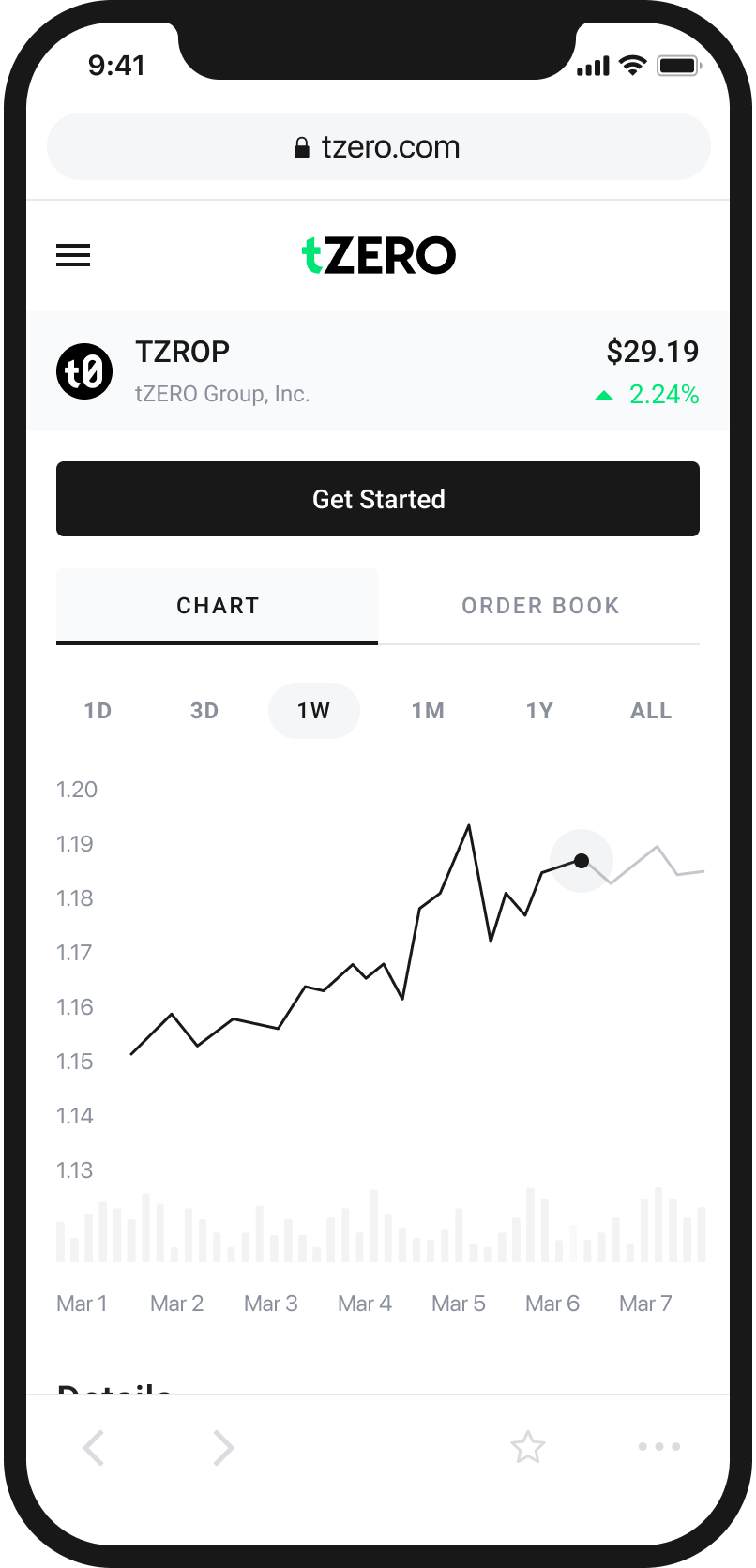
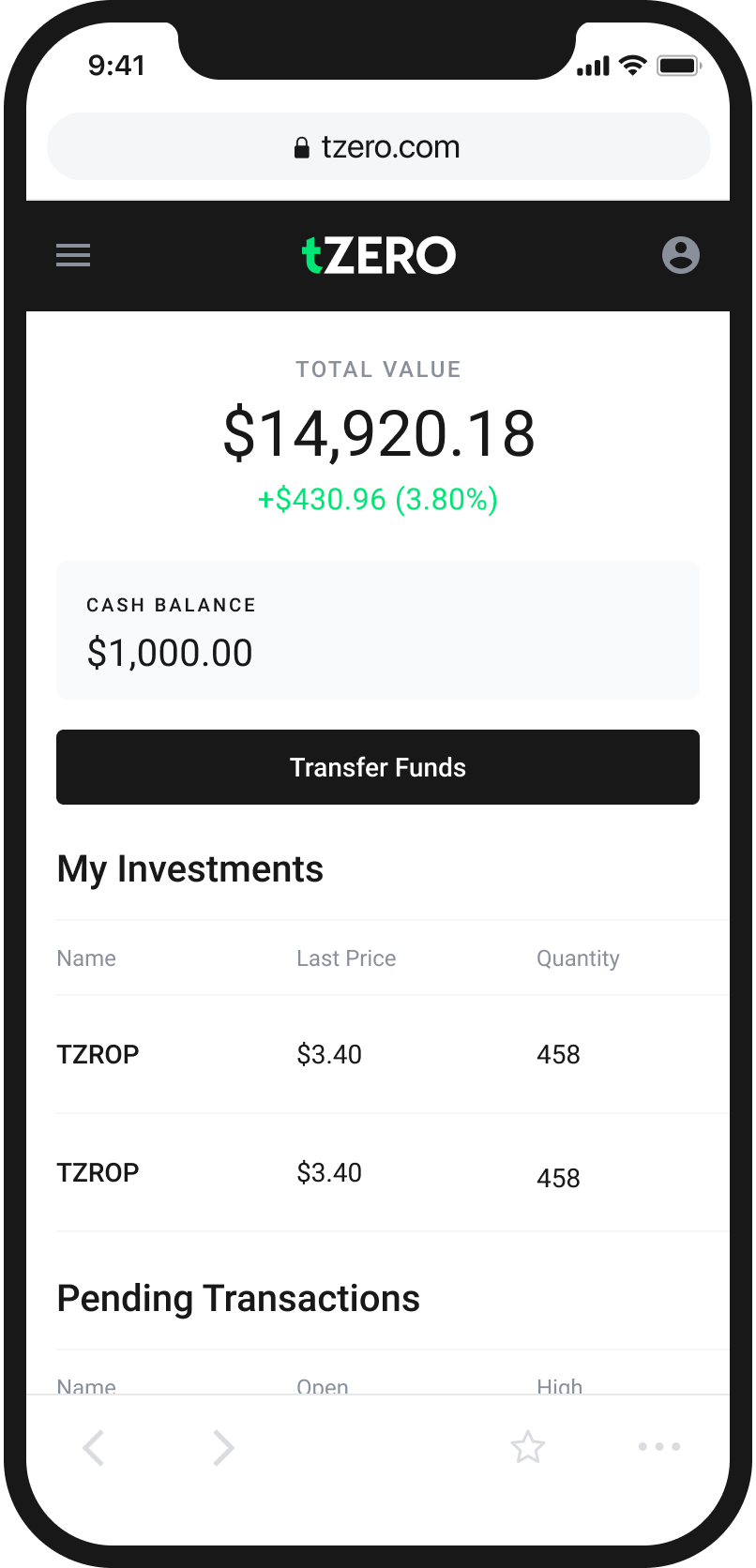
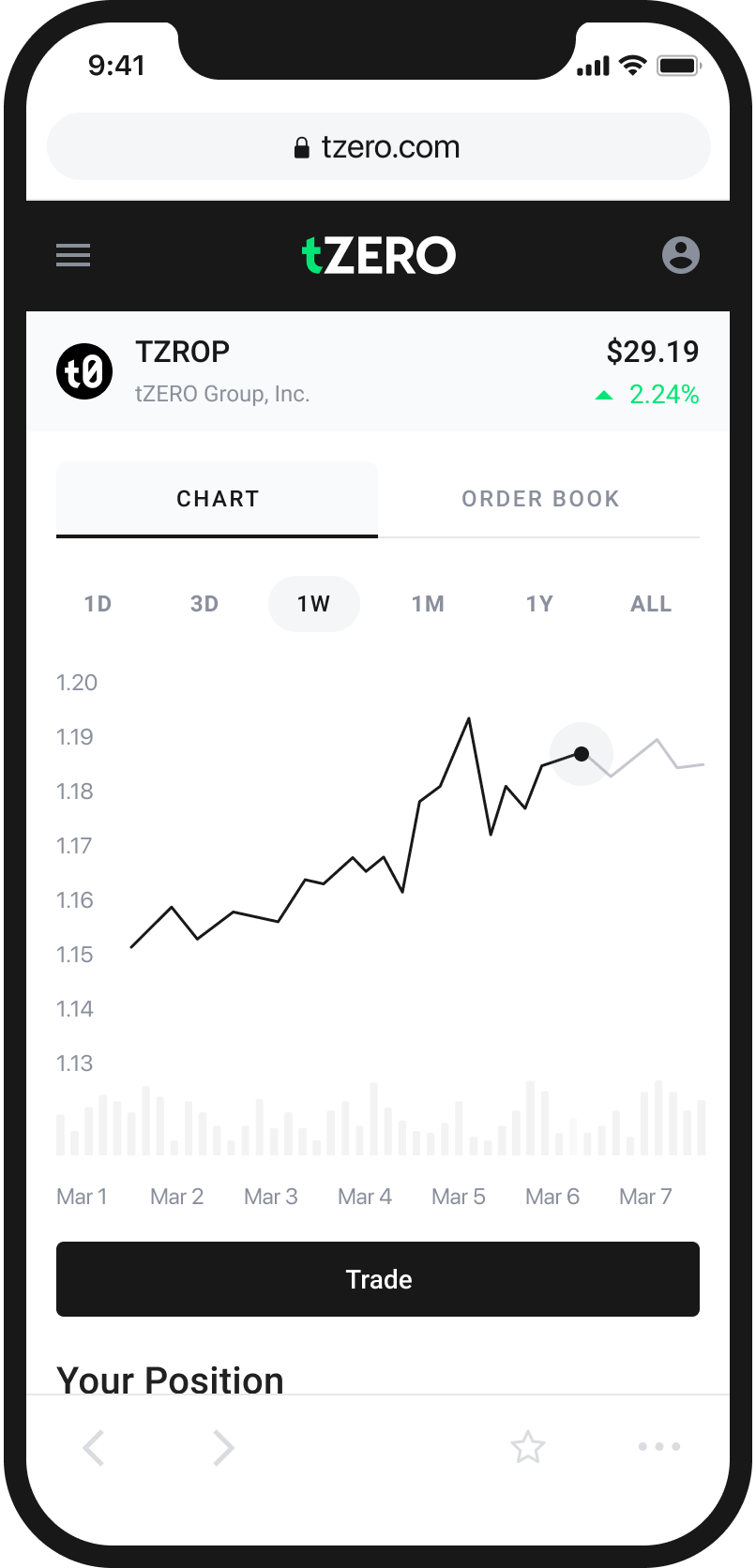
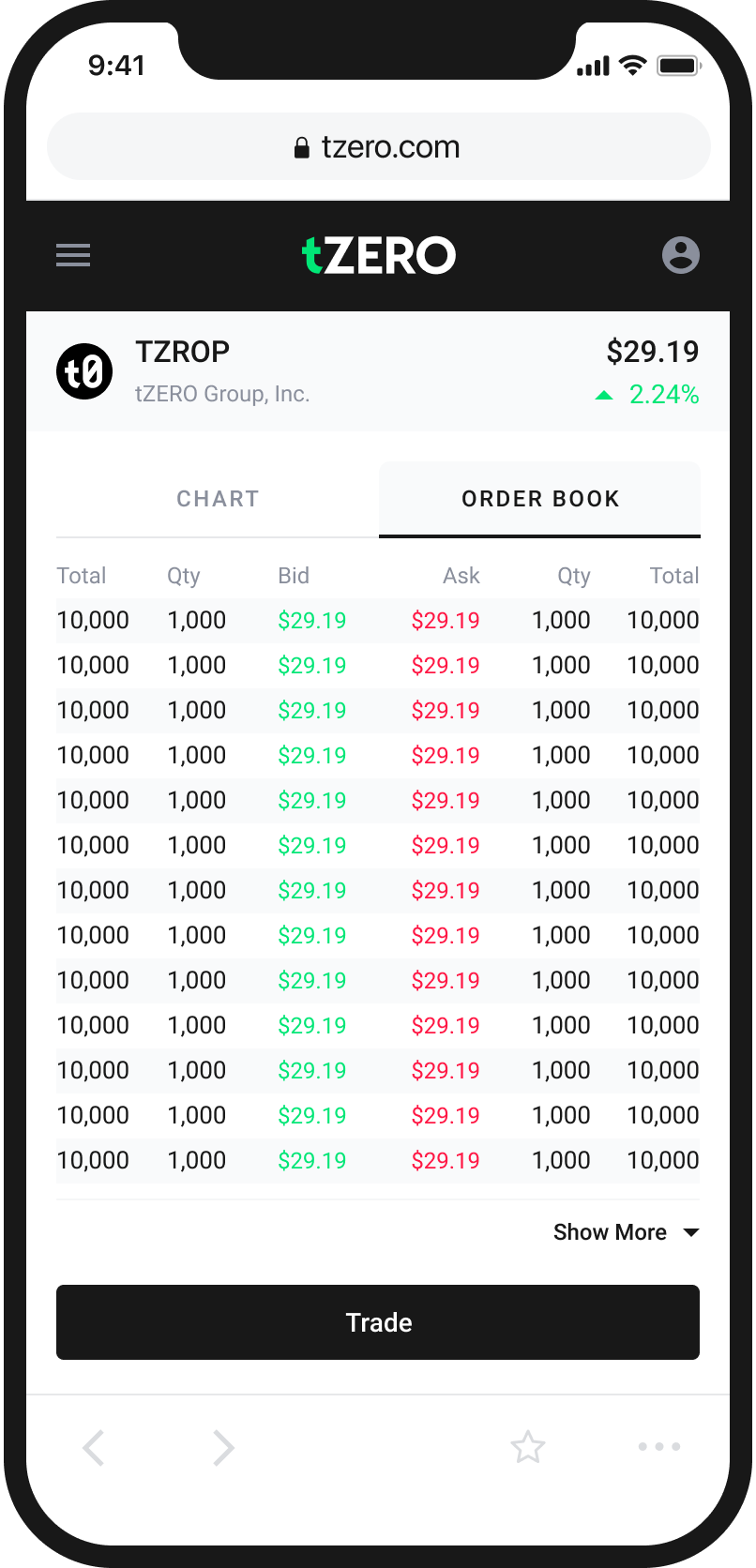
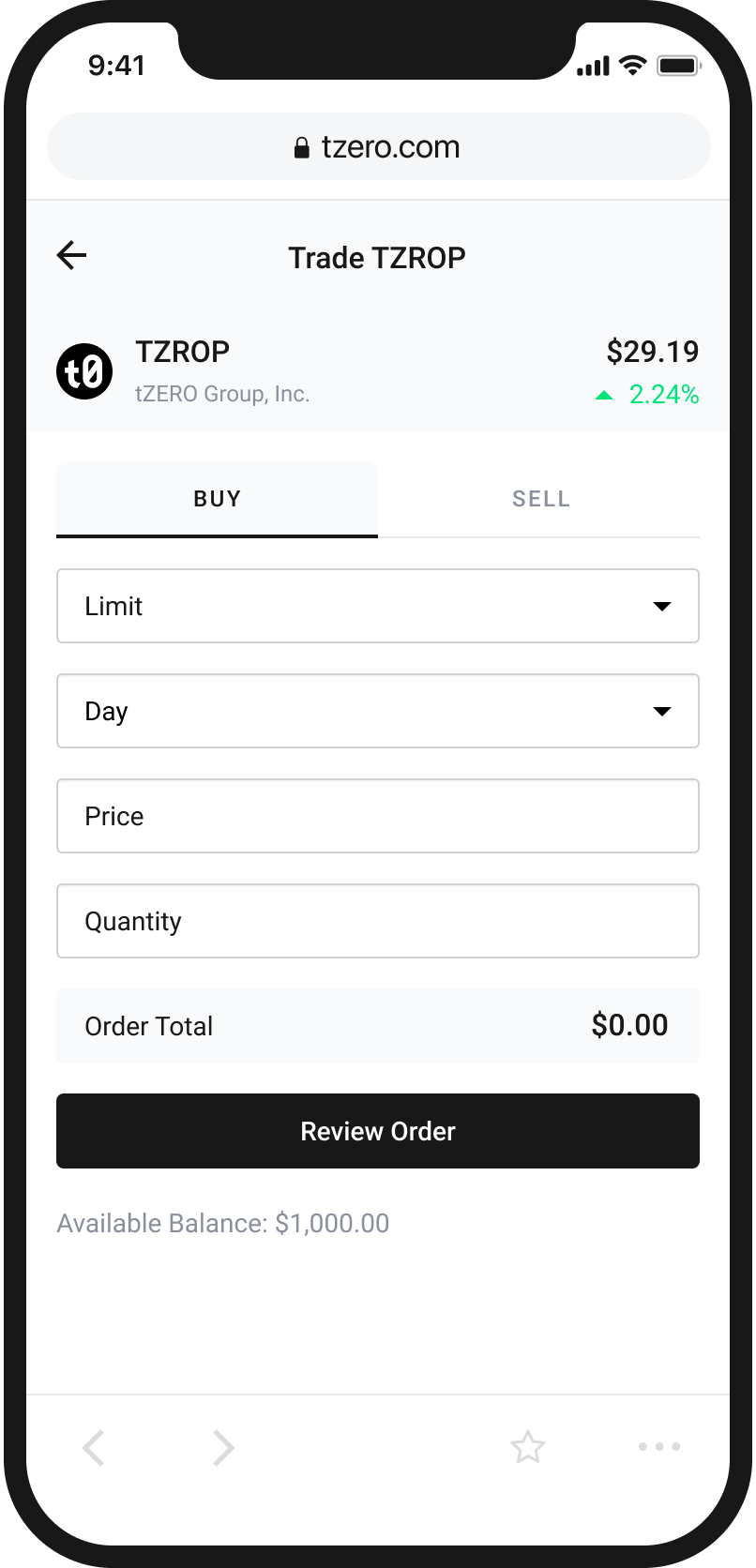
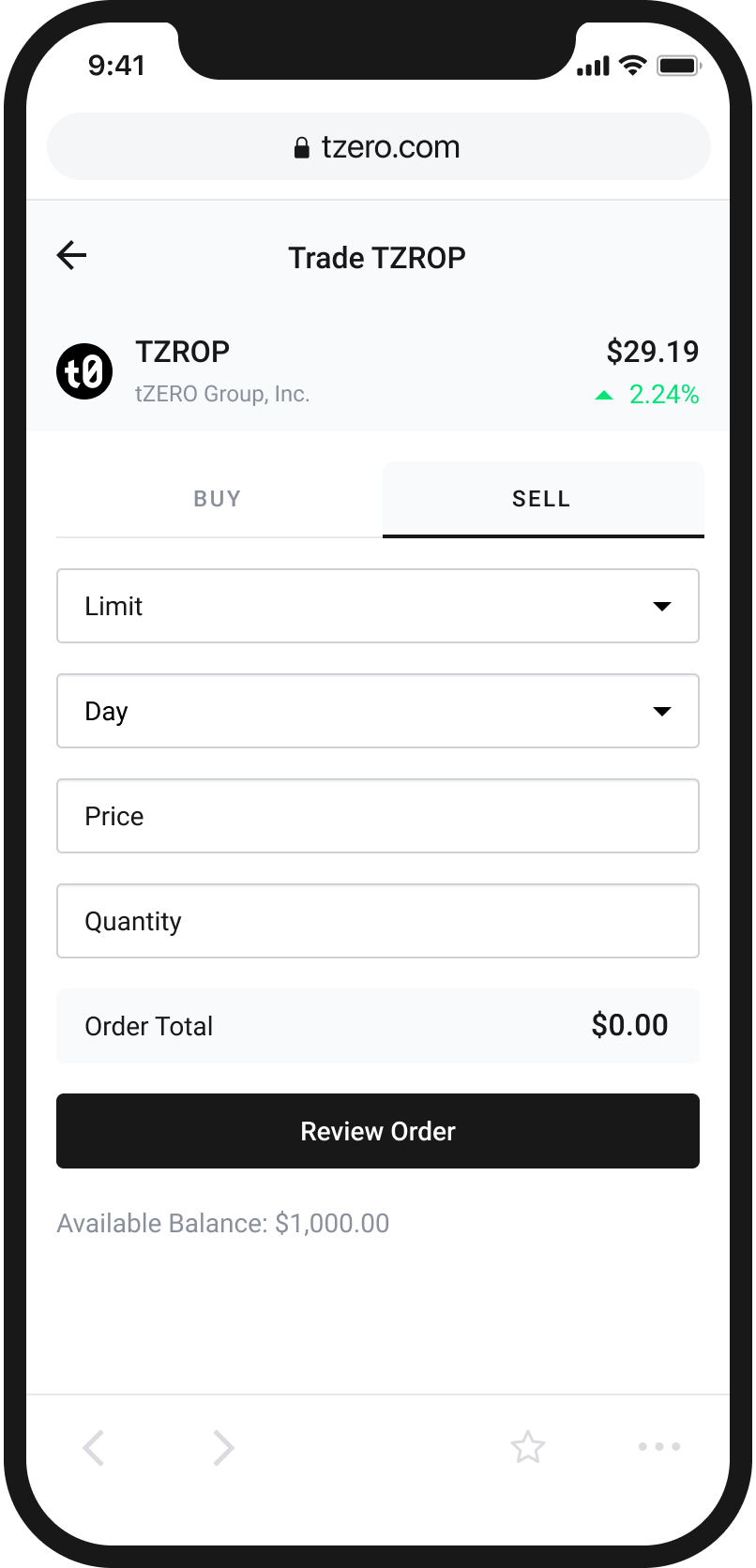
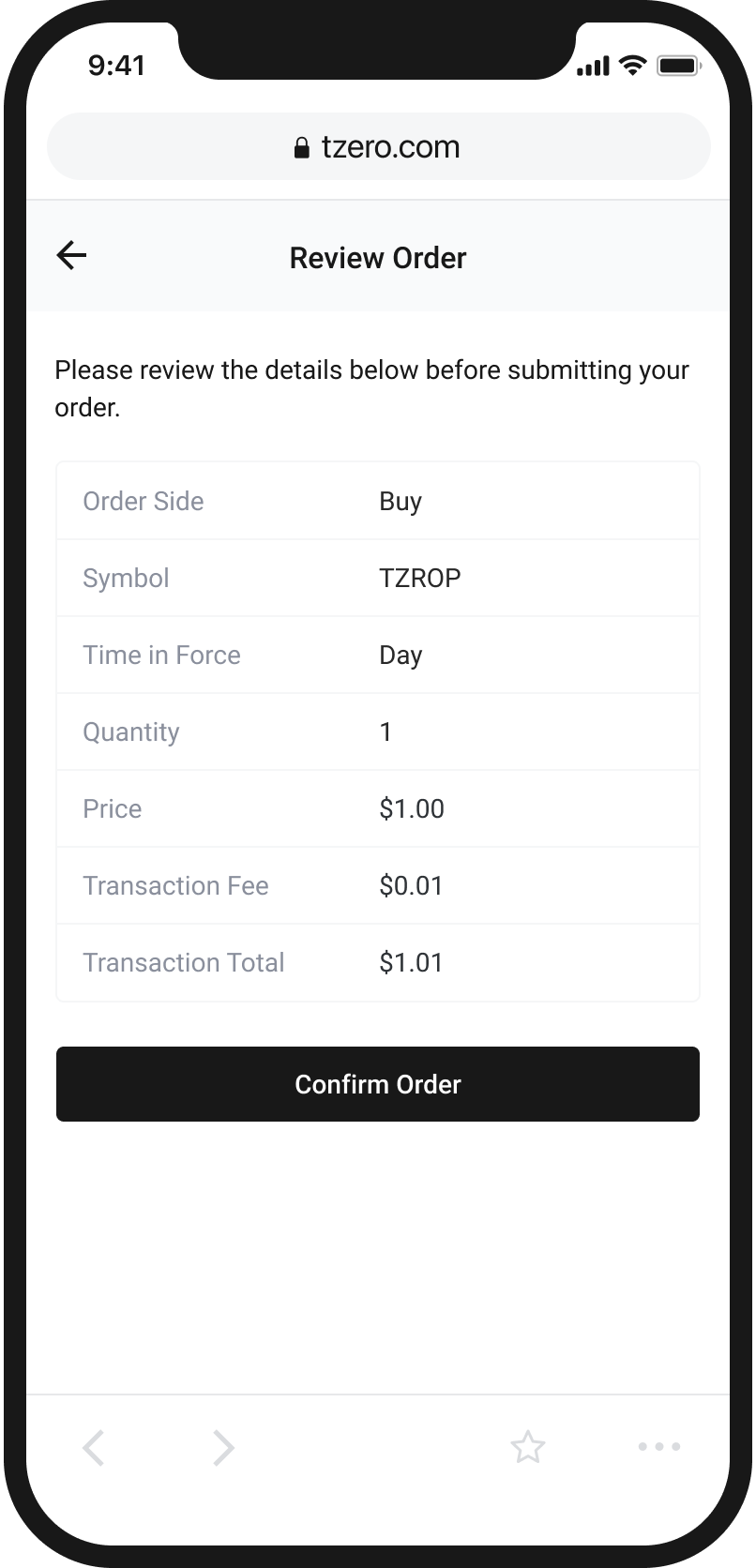
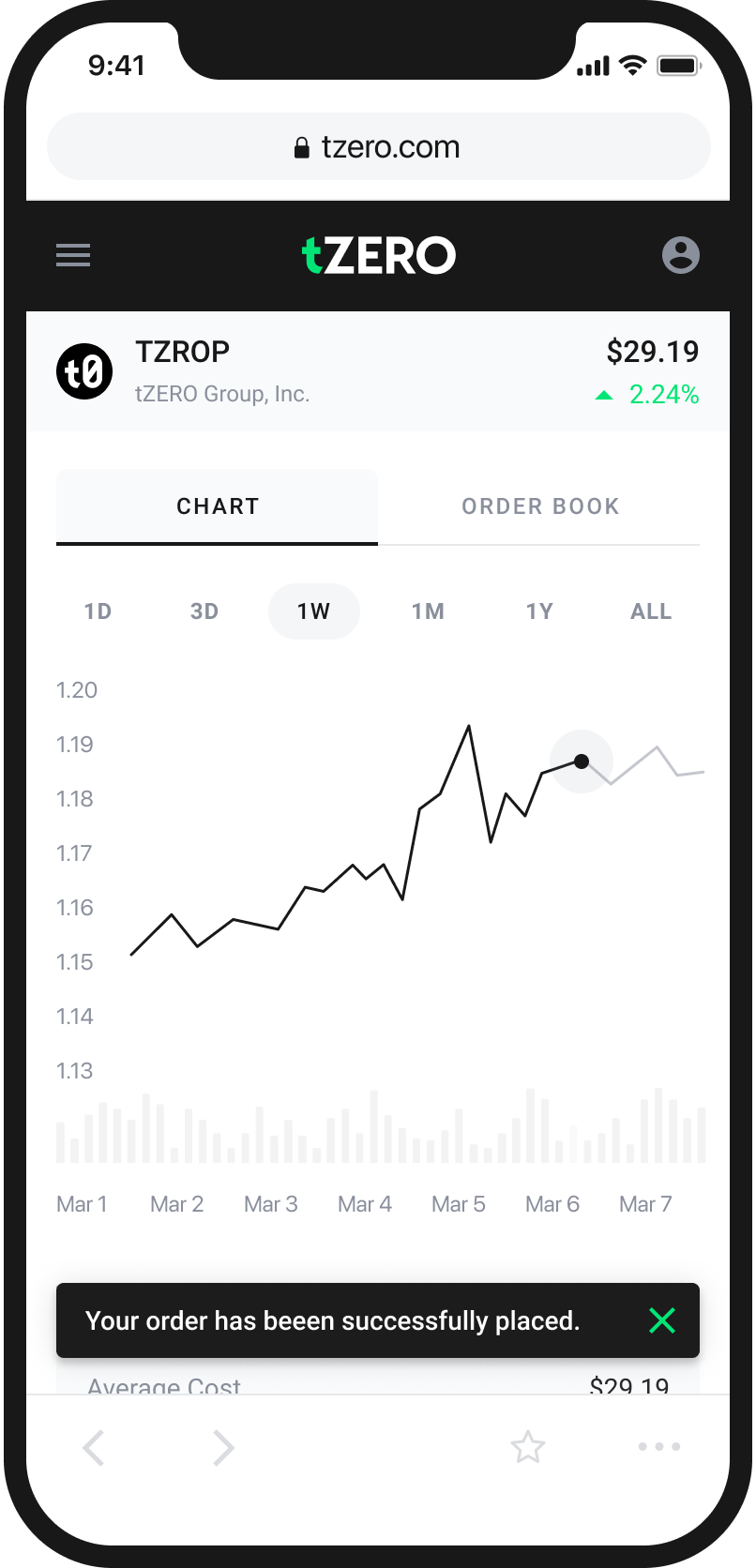
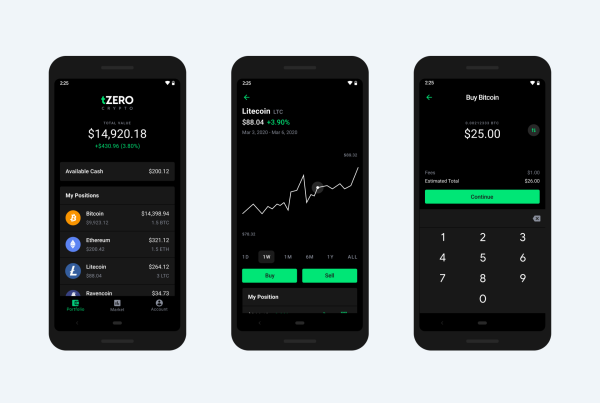
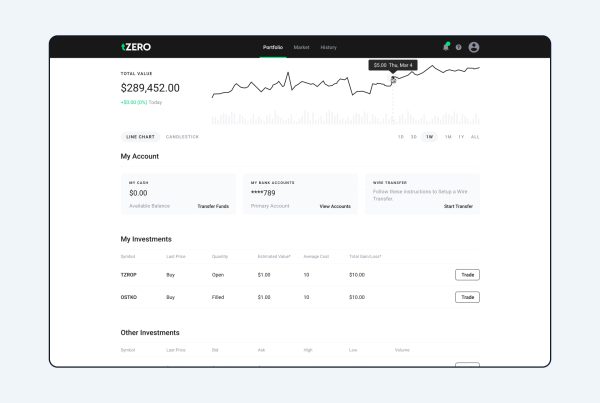
An Easy and Intuitive Way to Buy and Sell Cryptocurrency
With tZERO, your cryptocurrency is held in your personal wallet from the moment of purchase. This means only you have access to it and it cannot be hacked or stolen as long as you maintain control of your phone and password. Centralized exchanges hold the keys for you. This is convenient but can cause customers to lose their funds when hackers see large amounts of cryptocurrency in a single location or an exchange ceases to do business either temporarily or permanently. It also results in additional, hidden fees for the withdrawal of your cryptocurrency from the exchange.
A cryptocurrency wallet, like tZERO Crypto, is a software program or other method of storing cryptographic keys. These keys are required to transact with bitcoins or other cryptocurrencies. That means that keeping keys secure is of the utmost importance. Losing a key is like dropping cash on the ground or in a pond. This is why tZERO Crypto developed the Key Recovery system. It can help you get your money back if you lose your cryptographic keys.

Working together with cross functional partners in engineering and product management we found the right experience our investment tool would need to provide by matching the features necessary for a minimum viable product through User Story mapping and wireframing which helped us document the product roadmap.
Story mapping was a big step in our process. Story mapping is a method for arranging user stories to create a more holistic view of how they fit into the overall user experience. Within tZero and to accomplish a successful session we did the following activities.
- Sprint planning led by the product managers
- User stories written in high detail by the designer which included Relative Sizing using Affinity Estimating (small-large as card sizes)
- Historical task review to make sure our estimates are correct
- Acceptance criteria to each User Story was owned by the designer to help us understand what is allowed and determined as a success. If the acceptance criteria within a task is met we can call the task complete
Quick Timelines and Challenges
This project had a very short timeline so it was important that we had a strong wireframe in place. It was better that we spent time getting the wireframes correct to make sure we had a strong foundation going forward.
A challenge we found during wireframing was that our executive leadership team had a hard time visualizing the wireframes as they were hoping to see high fidelity designs and didn’t understand the process. Given wireframes are a two-dimensional illustration of a page’s interface that specifically focuses on space allocation and prioritization of content, functionalities available, and intended behaviors. We worked with product managers and we found a way to turn wireframes into a low fidelity flow that gave stakeholders a peak at what is to come while still respecting our process and goals.
With the design and development of our product well under way, we started on branding. We needed something bold that would stand out from competitors, while still feeling familiar to our investors.
Designing for Security in a Number of Ways
- Biometrics. Access to your wallet is protected with biometric data using your face and your fingerprint, ensuring that no one but you can access the wallet and the cryptocurrency stored on it.
- Transaction Verification. For every transaction, users are asked to take a picture of themselves so that we can verify the rightful owner of the account is the one authorizing the transactions. This picture is compared to the picture used in enrollment to verify that you are the person who owns your account. While no system is completely foolproof, this makes the security of the tZERO Crypto far stronger than other cryptocurrency wallets.
- Responsible Data Storage. To make sure we comply with state and federal laws, all new users will submit personal identifying information for analysis and approval. The personal identifying information collected by tZERO is not saved, so it cannot be stolen from tZERO. tZERO only keeps your name, picture, state and email address.
- Direct Delivery and Ownership. tZERO does not hold your cryptocurrency. When you purchase a Bitcoin from tZERO, it is sent from the point of purchase directly to your private wallet. Unlike many sites and exchanges, this means that no one can hack tZERO to steal your Bitcoin because we never have access to it.
- Disaster Recovery. Even if you lose your phone, tZERO has a unique, patentable way to recover your funds that no other service offers. While we hope this doesn’t happen, you can have peace of mind that even in an unfortunate event such as this, your money is still safe.